Fala Rapaziada, beleza?
Hoje vou trazer a resolução do Laboratório Preignition do Starting point do HTB.
Capture to Flag
Primeiro, rodei o nmap para descobrir as portas abertas. A única porta aberta é a 80 que está rodando um nginx 1.14.2.
nmap -sSV -p- -Pn 10.129.24.197 --min-rate=1000
Starting Nmap 7.93 ( https://nmap.org ) at 2023-02-24 08:54 EST
Nmap scan report for 10.129.24.197
Host is up (0.19s latency).
Not shown: 65534 closed tcp ports (reset)
PORT STATE SERVICE VERSION
80/tcp open http nginx 1.14.2
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 76.63 seconds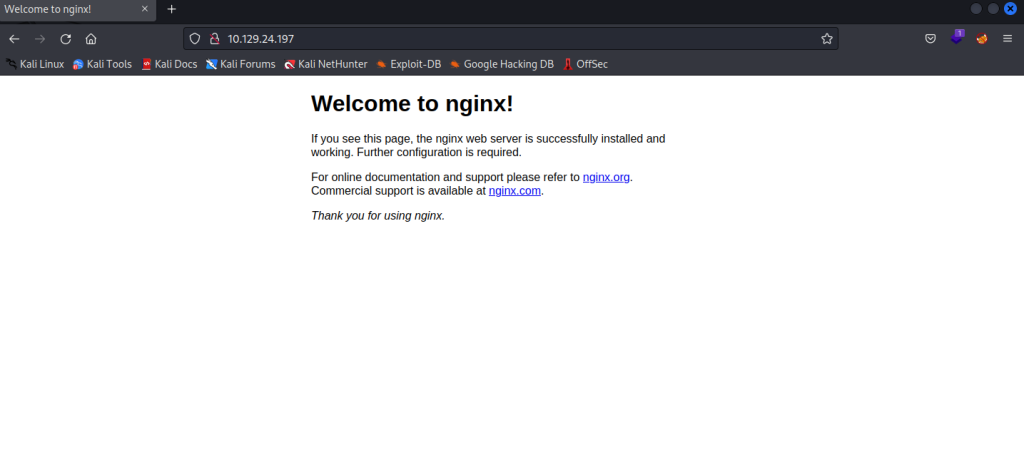
Na página principal não foi encontrado nenhum vetor de ataque, então parti para o brute force de diretórios com gobuster, colocando como extensão o php.
Encontrada a página admin.php
gobuster dir -u http://10.129.2.101/ -w /usr/share/wordlists/dirb/big.txt -x php
===============================================================
Gobuster v3.4
by OJ Reeves (@TheColonial) & Christian Mehlmauer (@firefart)
===============================================================
[+] Url: http://10.129.2.101/
[+] Method: GET
[+] Threads: 10
[+] Wordlist: /usr/share/wordlists/dirb/big.txt
[+] Negative Status codes: 404
[+] User Agent: gobuster/3.4
[+] Extensions: php
[+] Timeout: 10s
===============================================================
2023/02/24 12:22:19 Starting gobuster in directory enumeration mode
===============================================================
/admin.php (Status: 200) [Size: 999]
Progress: 40938 / 40940 (100.00%)
===============================================================
2023/02/24 12:35:15 Finished
===============================================================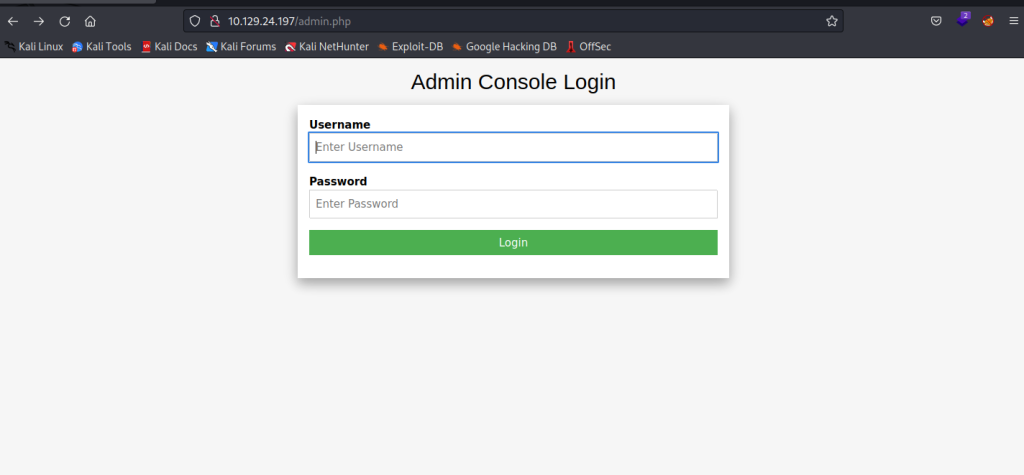
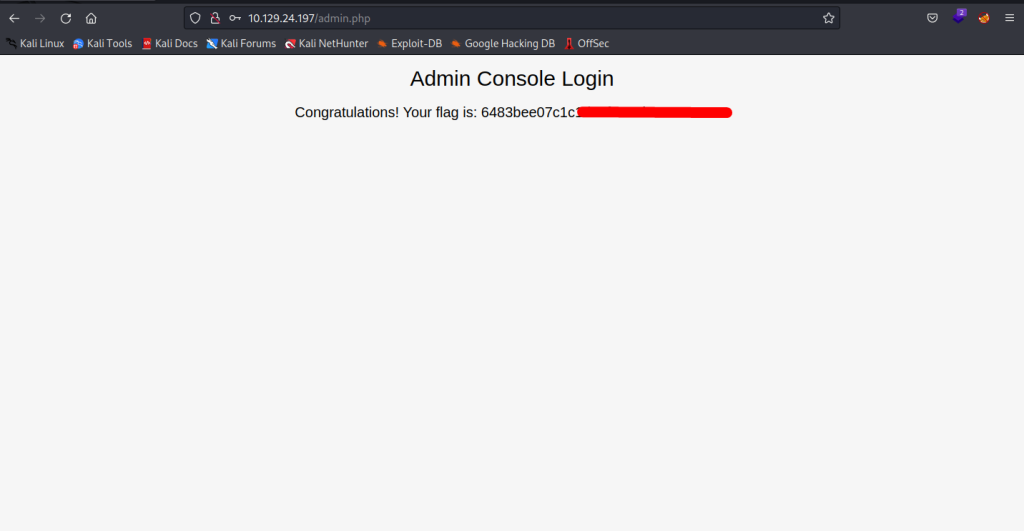
Acesso bem sucedido com as credenciais admin:admin, e capturada a flag.
Tarefas
TASK 1 – Directory Brute-forcing is a technique used to check a lot of paths on a web server to find hidden pages. Which is another name for this? (i) Local File Inclusion, (ii) dir busting, (iii) hash cracking.
R: dir busting
TASK 2 – What switch do we use for nmap’s scan to specify that we want to perform version detection
R: -sV
TASK 3 – What does Nmap report is the service identified as running on port 80/tcp?
R: http
TASK 4 – What server name and version of service is running on port 80/tcp?
R: nginx 1.14.2
TASK 5 – What switch do we use to specify to Gobuster we want to perform dir busting specifically?
R: dir
TASK 6 – When using gobuster to dir bust, what switch do we add to make sure it finds PHP pages?
R: -x php
TASK 7 – What page is found during our dir busting activities?
R: admin.php
TASK 8 – What is the HTTP status code reported by Gobuster for the discovered page?
R: 200




Seja o primeiro a comentar